SlowMist Named 3 Key Causes of Crypto Theft
07/04/2024 19:40
SlowMist's Q2 2024 report highlights key weaknesses in crypto security, focusing on private key mishandling, fake wallets, and honeypot scams.
SlowMist, a leading blockchain security firm, released its 2024 Q2 MistTrack Stolen Funds Analysis report, looking closely at cryptocurrency thefts in the second quarter of 2024.
Based on 467 reports of stolen funds, the firm revealed three key weaknesses led to cryptocurrency theft and explained the methods that users can utilize to protect their funds.
Private Key Leaks Top the List
According to SlowMist, the second quarter of 2024 saw a troubling increase in security incidents. During this time, users reported 467 cases of stolen funds, including 321 from Chinese sources and 146 from other countries.
The platform’s team helped 18 victims lock nearly $20.66 million worth of funds across 13 companies. Additionally, the firm discussed the main causes of these incidents.
The most common cause of crypto theft is the mishandling of private keys. Despite warnings, many people store their private keys in Google Drive and other cloud services. Some even send this data to friends through social networks and messengers. Hackers use credential stuffing attacks to log into these cloud services and steal private keys.
Read more: 15 Most Common Crypto Scams To Look Out For
Another common cause of private key leaks is fake wallets. These apps often replicate legitimate software exactly, tricking users into entering private keys and directly transmitting them to attackers.
“Despite being an old issue, many users still inadvertently click on ads while using search engines and download fake wallet apps. Many users choose to download applications from third-party sites due to network reasons. Although these sites claim that their apps are mirrored from Google Play, their actual security is questionable,” read the report.
Phishing also remains a major cause of theft in the crypto industry. According to SlowMist, about 80% of the first comments under tweets from prominent project accounts are occupied by scam accounts.
Read more: Crypto Social Media Scams: How to Stay Safe
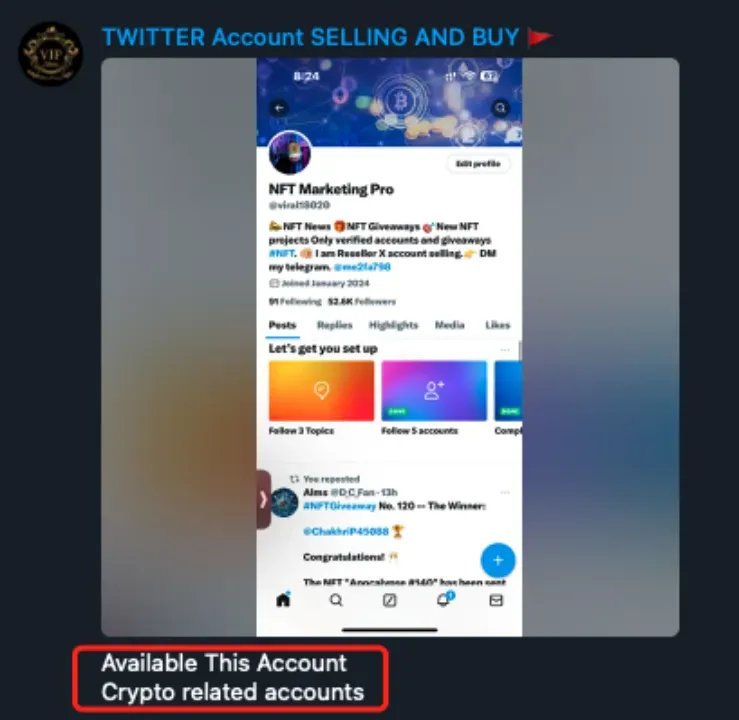
Fake X (formerly Twitter) accounts that spam under posts are sold in various Telegram feeds. Attackers can select profiles based on the number of followers and registration date. Most of the pages being sold are related to the crypto industry and crypto influencers. Experts also noted that some websites sell fake X accounts.
“For example, a fake account named ‘Optimlzm’ can look almost identical to the real account ‘Optimism’. After purchasing the highly similar account, phishing groups use promotion tools to boost the account’s interactions and follower count, thereby increasing its credibility,” SlowMist experts noted.
Honeypot Promises Mislead Crypto Users
The third threat identified by SlowMist is the honeypot scam. In this scheme, fraudsters create tokens that seem promising and offer high returns, but these tokens are programmed to be unsellable. This type of scam is particularly rampant on decentralized exchanges like PancakeSwap.
“I asked a question in a Telegram group, and someone enthusiastically answered and taught me a lot. They suggested I invest in a new token in the primary market and provided me with a contract address on PancakeSwap. After I bought it, the token’s value kept rising. They told me it was a once-in-six-months golden opportunity and urged me to invest more. When I asked others in the group to help investigate, I discovered it was indeed a honeypot token. I could buy but not sell it,” one victim shared with SlowMist.
Read more: Top 9 Safest Crypto Exchanges in 2024
To reduce these risks, SlowMist stresses the need for strong security practices. They recommend using blockchain explorers like Etherscan or BscScan, which offer insights through audit trails and user comments, and browser extensions like Scam Sniffer, which can detect and alert users about potential phishing sites.
The findings of this report highlight the ongoing vulnerabilities and underline the need for proactive security measures by all participants of the ecosystem.
Trusted
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.