Attackers Shifted from DeFi to CeFi: Cyvers' Web3 Security Report Q2 2024
07/08/2024 19:36
The Q2 2024 Cyvers Web3 Security Report reveals a surge in crypto attacks, shifting tactics, and significant financial impacts.
As Q2 2024 concludes, the Web3 ecosystem navigates a constantly changing security environment. This quarter has witnessed a significant shift in attack vectors. Centralized exchanges (CEX) have borne the brunt of major incidents, while decentralized finance (DeFi) protocols have shown improved resilience.
A report from blockchain security firm Cyvers provides a detailed analysis of security incidents. The report highlights their impact on various segments, changes in hacker tactics, and the economic repercussions of these incidents.
Rising Cyber Threats Drive Crypto Losses to New Heights in 2024
The Cyvers Web3 Security Report for Q2 and H1 2024 reveals a dramatic increase in crypto losses due to cyberattacks. The report notes notable events, shifting attack strategies, and financial and operational effects on the Web3 ecosystem. Despite the rise in attacks, recovery efforts and incident response strategies have shown improvement, showing the need for continuous vigilance and strong security measures.
Q2 2024 witnessed $629.68 million in crypto losses across various 49 incidents, bringing the year-to-date total to a staggering $1.38 billion as of H1 2024. This figure shows a notable rise compared to the same period in 2023, therefore highlighting the ongoing and changing character of threats in the Web3 environment.
Read more: 15 Most Common Crypto Scams To Look Out For
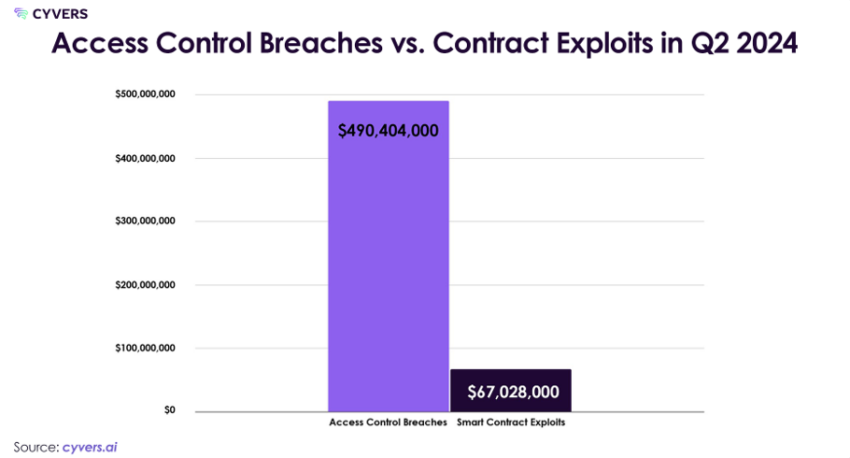
Smart contract exploits accounted for $67,378,000 from 20 incidents, while access control breaches resulted in losses of $491,311,000 from 26 incidents. Furthermore, address poisoning accounted for $71,475,000 of the 361 incidents. The year-over-year loss increase shows an over 100% rise from Q2 2023.
“It’s worth noting that the amount of funds recovered rose by almost 42%, from $138,900,000 in Q2 2023 to $197,000,000 in Q2 2024. This notable increase highlights the value of solid response techniques and improved recovery efforts,” the Cyvers team told BeInCrypto.
Crypto Hacks Impact in Q2: Regulatory Scrutiny and Rising Costs
However, the losses go beyond numbers. The security problems in Q2 had a wide and significant effect on the economy.
The high-profile CEX hacks have intensified regulatory scrutiny, potentially resulting in stricter compliance requirements and elevated operational costs for exchanges. As afflicted companies pursue legal action against the offenders, these events have also seriously tarnished their reputations and increased legal expenses.
Furthermore, adding to the running expenses of Web3 projects are the frequency and scale of attacks, which have sharply raised crypto insurance rates. Frequent security lapses could undermine user trust, lowering Web3 space adoption rates and investment.
The quarterly report from the Cyvers team also pointed out geographical trends in Web3 cybersecurity threats. Eastern Europe saw a surge in activity, while Asia-Pacific centralized exchanges faced targeted attacks due to regulatory gaps and weaker cybersecurity laws. On the other hand, North American DeFi protocols showed increased resilience, likely due to stringent security and compliance measures.
DeFi vs. CeFi: Comparing the Impact of Recent Crypto Attacks
In Q2 2024, there was a notable shift in security breaches towards access control incidents, particularly targeting centralized exchanges. This marked a move away from exploiting smart contract vulnerabilities in DeFi protocols. Access control exploits increased by 35%, while smart contract exploits decreased by 83% compared to H1 2023.
The dramatic 900% increase in CeFi losses compared to Q2 2023 signals a significant shift in attacker focus. This trend may be attributed to the concentration of assets in centralized platforms and potentially lax security measures in some exchanges.
The Cyvers team takes DMM Bitcoin’s incident as an example. The Japan-based centralized exchange suffered a significant hack in May 2024, resulting in $305 million in losses. This event marked the largest blockchain hack since December 2022 and the third-largest in crypto history.
The hack involved transferring 4502.9 BTC (over $308 million) to multiple addresses, complicating recovery efforts. Initially, the nature of the transfer was unclear. However, DMM Bitcoin confirmed it as a security breach and initiated an investigation.
It also assured customers that their deposits remained secure. Potential causes included compromised hot wallet keys allowing unauthorized transactions, attackers tricking users into signing malicious transactions, or seeding transaction histories with lookalike addresses to mislead users.
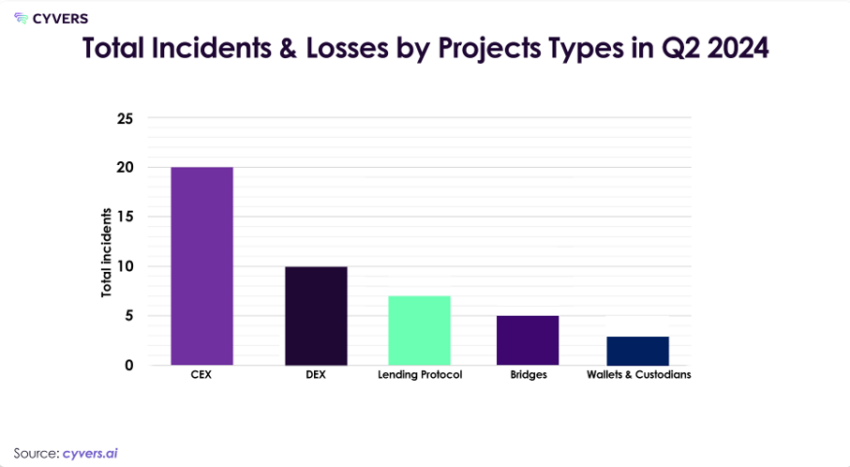
Meanwhile, in the DeFi sectors, the Cyvers team reported that decentralized exchanges (DEX) witnessed significant incidents. However, these were less severe than those affecting their centralized counterparts.
Lending protocols experienced moderate impacts, with notable incidents involving Sonne Finance and UwU Lending. The Cyvers team examined Sonne Finance’s exploitation, taking it as a case study.
“The $20 million exploit of Sonne Finance involved a complex oracle manipulation tactic. Attackers exploited a vulnerability in the protocol’s price feed mechanism, momentarily inflating the value of a lesser-known token. This allowed them to borrow against the inflated collateral and drain the protocol’s liquidity pools before the price could be corrected,” they explained.
Bridges emerged as an increasing target, with incidents like XBridge. Wallets and custodians also faced significant losses, with notable incidents like Coinstats.
From Address Poisoning to Oracle Manipulation: The Trends in Q2
The rise of address poisoning demonstrates attackers’ increasing cunning and highlights the need for enhanced security measures. Address poisoning can cause significant financial losses due to users’ trust in familiar addresses.
Other notable trends in Q2 2024 included flash loan attacks exploiting temporary vulnerabilities in liquidity protocols, oracle manipulation attacks exploiting price feeds for arbitrage opportunities, and cross-chain attacks leveraging weaknesses in bridge protocols to siphon funds across chains.
The quarter also saw evolving sophistication in post-attack money laundering techniques. Attackers increasingly used cross-chain bridges to move stolen funds across multiple blockchains, complicating tracking efforts.
New DeFi protocols offering privacy-enhancing features were exploited for money laundering purposes. AI algorithms are being employed to automate and optimize the movement of stolen funds, rendering traditional tracking methods less effective. There has been an increased use of privacy coins, decentralized mixers, and sophisticated methods to obscure transaction trails, including cross-chain swaps and layer 2 solutions.
Rapid Response Mitigates DeFi Losses in Q2 2024
Effective incident response strategies observed in Q2 2024 included quick action to freeze vulnerable contracts and minimize losses in several DeFi incidents. Cyvers noted that some DeFi protocols successfully implemented decentralized security teams that could quickly respond to and mitigate threats.
For instance, improved coordination between exchanges, blockchain analytics firms, and law enforcement led to the recovery of $22 million from the Gala Games hack. Additionally, pump.fun, the meme coin creation platform on Solana, demonstrated rapid response after their security breach, including immediately pausing the contract, engaging with the hacker through on-chain messages, and offering a bounty. Their proactive measures resulted in 80% of the stolen funds being returned within 24 hours.
Cyvers Predicts Rising Attacks on Layer 2 Solutions and Gaming Platforms
Based on Q2 trends, the Cyvers team predicts several threats to emerge in the future. These include a continued rise in sophisticated contract exploits, the integration of AI in attack vectors, increased risk to current cryptographic standards as quantum computing advances, increased targeting of Layer 2 solutions with their growing adoption, and the potential for attacks that exploit vulnerabilities across multiple chains. Additionally, there is a possibility of more attacks on gaming platforms and NFTs.
As the ecosystem becomes more interconnected, security audits need to be considered for improved cross-chain interactions. Leveraging AI for real-time threat detection and response, fostering greater information sharing and collaborative defense mechanisms across the industry, and adopting multi-layered security protocols are essential.
Read more: Top 5 Flaws in Crypto Security and How To Avoid Them
User behavior continues to play a crucial role in security incidents. Phishing and social engineering remain significant factors in security breaches. Weak passwords and password reuse continue to be exploited in attacks. Users granting unnecessary permissions to smart contracts remain a significant vulnerability.
Regular security awareness campaigns, best practices for private key management and multi-factor authentication, wallets and DApps implementing real-time warnings for suspicious transactions, and peer-to-peer education programs within crypto communities have effectively raised security awareness.
Trusted
Disclaimer
Following the Trust Project guidelines, this feature article presents opinions and perspectives from industry experts or individuals. BeInCrypto is dedicated to transparent reporting, but the views expressed in this article do not necessarily reflect those of BeInCrypto or its staff. Readers should verify information independently and consult with a professional before making decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.